The goal of the Coronavirus geotracking- or Bluetooth tracking and phone data analysis is to determine and break infection chains as quickly as possible. The key challenge in this special apps is to motivate citizens to download the app. An alternative to Coronavrius tracking apps is to rely on third party data of operating system providers or third party apps. We discuss the different solutions available and present concepts on how to implement these solutions.
Why third party location tracking
The continous developments and impact of the Coronavirus fasttracked the economy into a recession. The spread of the virus has put forward the option of extended tracking with third party data on discussion tables.
Apps which are developed for the pure cause of tracking Coronavirus cases need effort to be developed effectively and marketed in order for citizens to want to install them.
App installations cost between 1.22 up to 4,08 USD and we believe that even when a Coronavirus geotracking app or even a privacy compliant Coronavirus Bluetooth tracking app with a fance Blockchain backend gets rolled out, there will be a challenge in getting people to install an app.
Rather than forcing citizens to install such an app and the complications that come with developing such an app, an alternative method is to leverage data and apps which are already present. Several governments already utilize surveillance and digital tracking in some form to support the fight against the Coronavirus.
It might also be that some secret agencies who monitor the Coronavirus already utilize their tracking capabilities or do it in the future.
Since there are secret agencies worldwide and we do not know which data they really have or use we focus purely on the “how it can work” and keep the moral aspect aside.
Who has precise location information?
There are several players who have apps which require active access to the following:
- GPS locations of users
- Bluetooth access
- Connected WiFi Networks and WiFi Scanning
In the following, we describe a few companies and apps who posses location data of users.
OS Providers – Alphabet and Apple
Receiving a GPS location the first time on a day takes at least 30 seconds and it can go up to two minutes.
Therefore, iOS and Android have the feature that WiFi and other location signals can be transmit to Apple and Google to get a faster location fix.
Demonstrated below is the whole process of how operating system work to gain access to user locations:
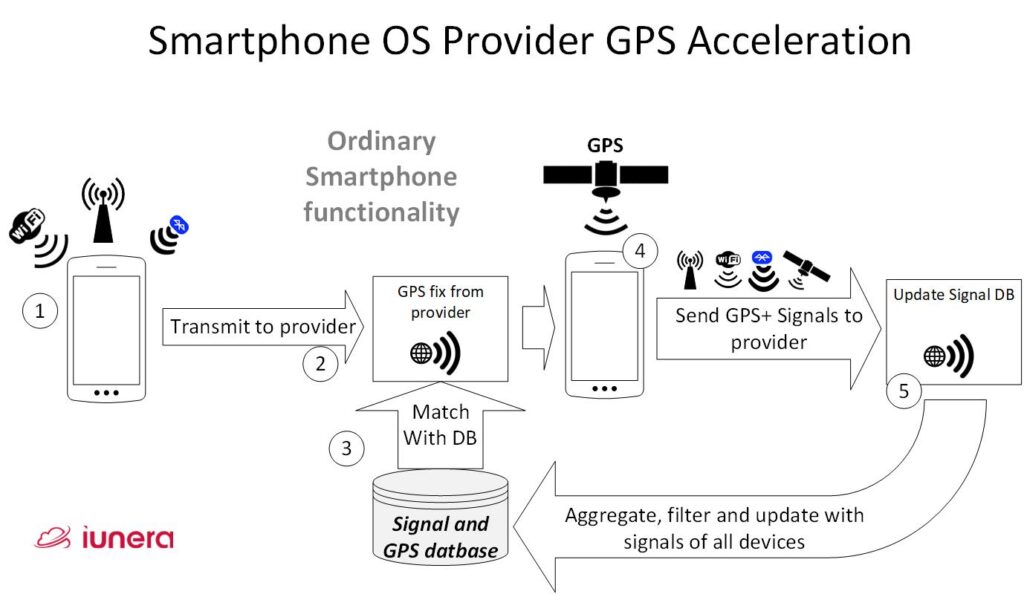
- First a mobile phone receives signals of Bluetooth devices, cell towers and WiFi near its location.
- All of the information is assembled together and submitted to the operating system provider API in the internet.
- The operating system provider has a database available which matches signals to GPS positions and gives the smartphone a triangulated GPS location out of the database.
- Finally, the GPS chip of the smartphone receives a GPS signal from the satellites.
- All the received WiFi networks, Bluetooth signals and other location relevant data is packaged together and sent to the operating system provider. The operating system provider uses this information to update the internal database.
You can find a public source code repository on how the WiFi in Android are collected in earlier Android versions before it was a part of the place services. We show an excerpt of this in the following code. In detail, we see how WiFi are collected before their data is then sent to an API.
// Wifi profile
if (mWifiScanResults != null && mWifiScanResults.size() > 0) {
ProtoBuf wifiProfile =
new ProtoBuf(GwifiMessageTypes.GWIFI_PROFILE);
wifiProfile.setLong(GWifiProfile.TIMESTAMP, scanTime);
wifiProfile.setInt(GWifiProfile.PREFETCH_MODE,
GPrefetchMode.PREFETCH_MODE_MORE_NEIGHBORS);
int count = 0;
for (ScanResult s : mWifiScanResults) {
ProtoBuf wifiDevice =
new ProtoBuf(GwifiMessageTypes.GWIFI_DEVICE);
wifiDevice.setString(GWifiDevice.MAC, s.BSSID);
wifiProfile.addProtoBuf(
GWifiProfile.WIFI_DEVICES, wifiDevice);
count++;
if (count >= MAX_WIFI_TO_INCLUDE) {
break;
}
}
requestElement.setProtoBuf(
GLocRequestElement.WIFI_PROFILE, wifiProfile);
}To keep things short and straightforward: The telemetry data which a smartphone transmits to the operating system provider is more or less the same like we described in our article; how an app can collect data for Coronavrius tracking. All in all, WiFi, Bluetooth and other information that can help to fingerprint a geo location is sent to a backend API.
Mozilla and the open source community
Another and more indie option is to team-up with the Mozilla foundation who also runs a location project to assemble a free and open database of GPS positions together with Cell tower, WiFi and Bluetooth data.
There are also different apps which can collect the location information for the Mozilla location project. One popular examples is the Firefox browser.
The Mozilla foundation is very popular for privacy. This variant would have the advantage that when it is done the right way, the tracking service could be implemented transparently and open source in the most privacy compliant way.
Well distributed apps
Broad and wide distributed apps like Facebook who can access WiFi and and Bluetooth connection data can also be a location data source.
There are many such popular apps who can access WiFi or Bluetooth aside from Facebook. For instance, TikTok, VK, Microsoft mobile Android Word, sports club apps, ride sharing apps like Grab in Southeast Asia or Uber in other locations. Additionally, there are more popular apps which ask for WiFi, GPS or Bluetooth permissions during use.
Therefore, there are a number of possibilities to gain information from different apps which could then be used for tracking purposes.
Operating systems offer most data
In short, different third party apps require different integrations.
All in all, the key concept is always down to transmitting telemetry data with signals and GPS in an app to a backend and duplicating these time series data stream then for a second use in the form of Time Series analysis. We describe how to do time series analysis with such telemetry data in detail in another article.
The way to get most telemetry data is to use the operating system location services. The main advantage is that nearly all people have already opted in to transmit the telemetry data in exchange for a faster GPS location, and the operating system runs on every phone.
Additionally, the described location and telemetry transmission process is active regularly in the background of most smartphones, which means that there is always fresh and actual location data available.
In order to integrate advanced Time Series analysis an implementation can tap into operating systems backends or the operating system vendor can extend their internal process themselves and log the Time Series Data into a Time Series Database.
Android and iOS backend extension concept
There are different ways how extensions could be realized to duplicate the stream of location data. In the following, we present the one way that we consider ourselves as the fastest to implement and roll out.

In order to extend a location signal backend (that we described above) for Coronavirus tracking the following extensions are needed:
- Once a smartphone sent the location information in step 3 or 5 to the database of the operating system vendor, this telemetry data stream can be duplicated or transformed into a geo-fingerprint and logged into a Time Series Database. We describe this process in depth in our Time Series Database article. Thereby some mapping of the smartphone account to an anonymous ID is executed.
- When a person is infected with the Coronavirus, through the prior mapping it is possible determine the anonymous ID.
- The ID of the infected person gets prepared to match it with the time series data of location updates.
- The records of the infected person are compared with the telemetry of the non infected people and the possibly potentially infected people get determined.
- Out of this matching process, infection chains can be computed. Such infection chains can based on the logic that when people were most likely near an infected individual then they are carriers from that moment forward too.
- Out of the infection chains and the geolocation telemetry of the potentialy infected people, geolocations can be computed and the society and the potentially infected individuals can be notified.
Discussion
We discussed why smartphone third party Coronavirus geotracking can overcome the problem of expensive special Coronavirus app installations. Succeeding, we saw that mobile operating system providers and popular apps are potential sources for location information from WiFi and Bluetooth signal data. As an example, we described how location services of smartphone operating system providers can be extended to extract Time Series Data.
Ultimately, the Time Series location data is already present in the backends of various companies and in theory this data can be leveraged to do location analysis in the same way how it can be done with a separate Coronavirus specialized app.
For the final Big Data analysis after data extraction form the third party provider, the same methods like for a specialized Coronavrius geotracking app can be applied.
Even still, the issue of privacy compliance and non-consented users remains. Therefore, we believe that it can be an option to let third party apps or operating system providers ask for user consent with a pro active notification.
However, legality and privacy tresholds differ from country to country. This does not have a generic answer.
We might not be able to clarify the legal or ethical questions in this technology blog. Alternatively, we provide assumptions about the paracticability of a general roll out when legal questions are solved.
The likelihood to get more users to opt-in with a short popup via an app or operating system that they already use is probably successful to a rate that goes over 50 percent of the population.
Getting over 50% of the population of a country to install and trust a new app when compared to a short consent popup is much less likely to happen and harder to accomplish.
Last but not least, working third party apps are already rolled out and the project and bug risk that arise is minimal for the end user out of software stability.
Hence, third party Coronavirus geotracking can be a very quick option to roll-out and work with user consent. Key question are the transparency, implementation supervision and abuse control topics which need to be solved by compliance and governing methods.
Update (29th April 2021): Check out our latest project, Fahrbar!
Get in touch with us
If you are interested in Fahrbar or want to find out how we can help you leverage your data
